Dispatcher Paragon Spooler Controller
This section describes how to set the Dispatcher Paragon Spooler Controller so that it uses encrypted communication towards an SMTP server. The required steps are:
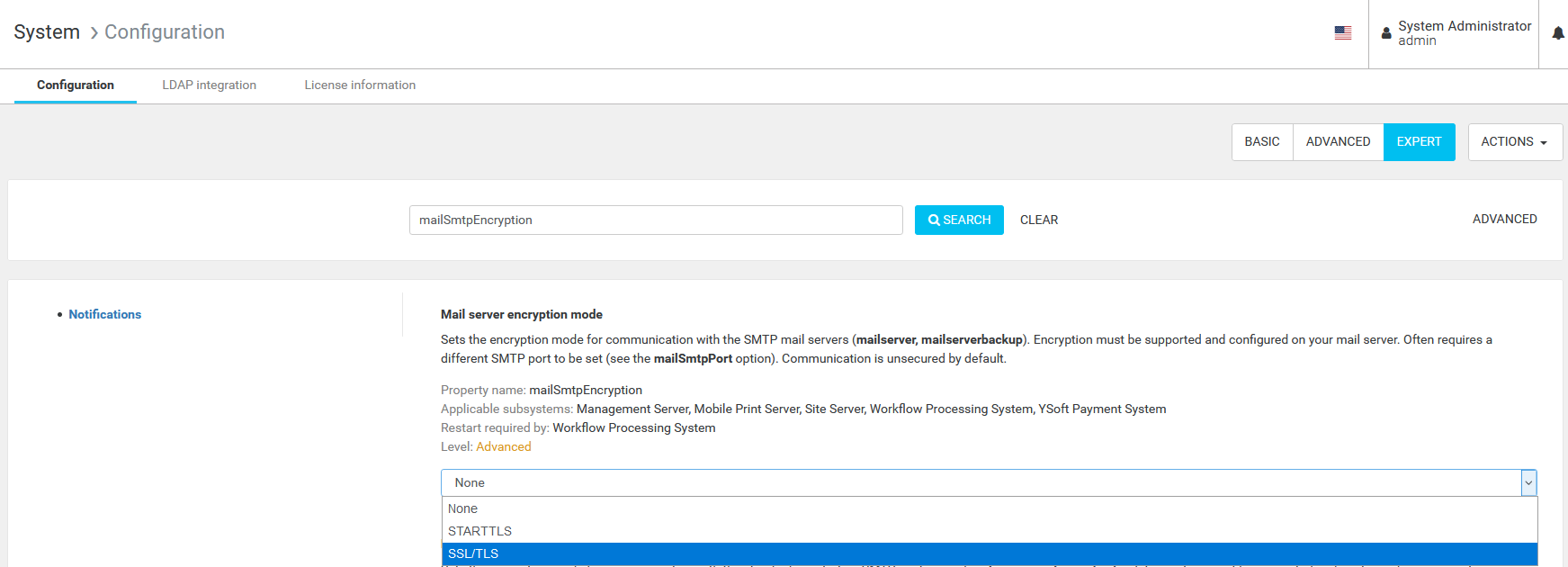
- enable the encryption via the mailSmtpEncryption parameter
- set the right SSL/TLS version for your environment (the default TLSv1.2 is usually ok)
- (OPTIONAL) if needed, one could also add a certification authority to the server's trust store, only in case of connection to a non public service. This step is not needed if connecting to public services like Office365.
How to configure encryption
In order to enable encryption, one has to connect to Management Server and set the "" parameter to SSL/TLS or STARTTLS, as shown in figure
It is possible to tune the configuration of each Dispatcher Paragon Spooler Controller separately, if they need to have different values, for example, if the Dispatcher Paragon Spooler Controller is installed in a branch.
You can configure Dispatcher Paragon Spooler Controller by using the following properties in spoc.conf . The default position of the configuration file is
<install_dit>\SPOC\conf\modules\spoc.confSMTP Properties for Spooler Controller Server
The following properties can be set in spoc.conf , to tune the behavior of the local server:
Parameter name | What does it do | Ex: Value |
|---|---|---|
mailserver | the address of the mail server to connect to | ex: smtp.example.com |
mailserverbackup | the alternative server to connect to | ex: alt-smtp.example.com |
mailfrom | the email sender, as it will be seen by the receiver of the mail | no-replay@example.com |
mailuser | the username that will be used to authenticate to the mail server | sample.user |
mailpass | the password that will be used to authenticate to the mail server | a strong password |
mailSmtpEncryption | the encryption protocol that will be used to connect to the send mail server |
|
mailSmtpPort | the port that will be used to connect to the send mail server | 25 |
mailSmtpConnectionTimeout | the timeout that will be used while connecting to the send mail server | 10000 |
mailSmtpTimeout | the timeout that will be used sending an email to the send mail server | 10000 |
Note:
If one leaves the value empty like in the following snippet:
mailuser =Then the server will use the value sent by the Dispatcher Paragon Management Server. In order to force the value to be really empty, one needs to use the special [EMPTY] keyword, like in the following:
mailuser = [EMPTY]How to configure SSL/TLS - STARTTLS for secured communication
Dispatcher Paragon Spooler Controller support both TLS and STARTTLS
Protocol | What does it do | Pros And Cons |
|---|---|---|
STARTTLS | Dispatcher Paragon Spooler Controller initiates a plain SMTP connection and asks the send mail server if it supports encryption, via the STARTTLS command.
| Pro: can be used when one does not have control on the settings of the SMTP server, or when such server needs to be also able to communicate in unencrypted mode with some legacy device. With this setting, secure and plain communication happen on the same port. Cons: if an attacker would impersonate the mail server, this approach would result in the attacker getting control of the email, without any visible error. |
SSL/TLS | Dispatcher Paragon Spooler Controller connects to the send mail server through secure connection directly. SafeQ fails to send messages if SMTP over SSL/TLS is not supported on the configured port. | Pro: in conjunction with enabling server certification, this setting offers the maximum protection to the mails sent. Cons: such setting is not according to SMTP standard and different ports for secure and plain communication are required: some servers don't support that. |
The value for this parameter depends on the deployment. Please first try "SSL/TLS", and downgrade to "STARTTLS" only if the send mail server does not support SSL/TLS. Note that the correct port needs to be configured based on the protocol selected. A mail server might support both protocols on different ports (e.g. SSL/TLS on 465 and STARTTLS on 587).
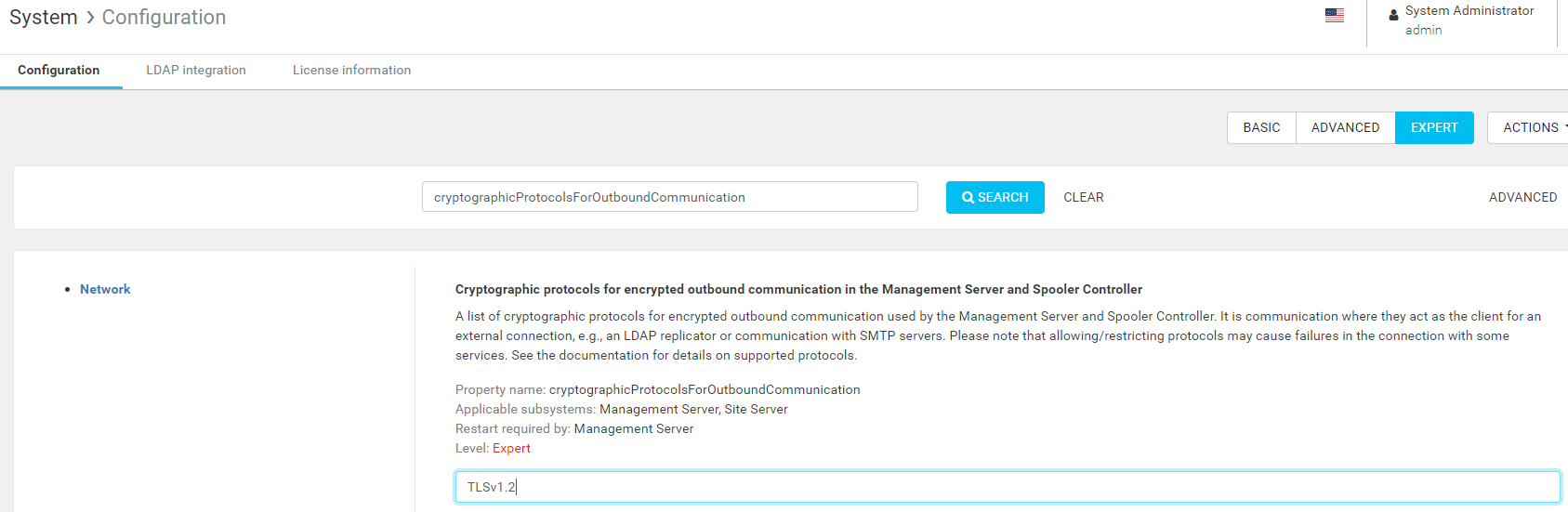
Which versions of protocol encryption are supported and how to configure it.
The supported versions of the TLS encryption protocol are TLSv1.3, TLSv1.2, TLSv1.1 and TLSv1. The default value is TLSv1.2. Those versions can be configured by cryptographicProtocolsForOutboundCommunication configuration value in the Management Server web interface:
Custom TLS ciphersuites can be configured by customCipherSuitesForOutboundCommunication which is applied when allowCustomCipherSuitesForOutboundCommunication is configured. This list contains recommended ciphersuites for TLS 1.2 by default. If a different protocol version is selected, the list of ciphersuites needs to be adjusted or allowCustomCipherSuitesForOutboundCommunication set to disabled to select ciphersuites automatically.
NOTE: This setting also applies to secure communication with other external systems such as LDAP. Be sure that your LDAP server, if you have one, also supports a more strict protocol, in case you decide to change this parameter to TLSv1.3.
How to configure certificate validation enable/disable.
SafeQ does not offer a way to disable server certificate validation: in order to use a self signed certificate, the root CA needs to be added to Dispatcher Paragon's trust store.
In order to add a certificate to the trust store of the Dispatcher Paragon Management Service, one needs to run the following command
keytool -import -keystore <path to the trust store> -file <root certificate> -alias <a name for the certificate>The default position of the trust store is
C:\DispatcherParagon\SPOC\conf\ssl-truststoreFor more details, please refer to System communication hardening, in the "Installing your Root CA to trust stores of Dispatcher Paragon machines" section, in the "Java Truststore" section.