- Provide a private key and certificate (.key and .crt files) on both machines.
- Configure any non-server clients to trust the certificate's root signing authority. For more information please see: https://support.microsoft.com/en-us/help/316898/how-to-enable-ssl-encryption-for-an-instance-of-sql-server-by-using-mi
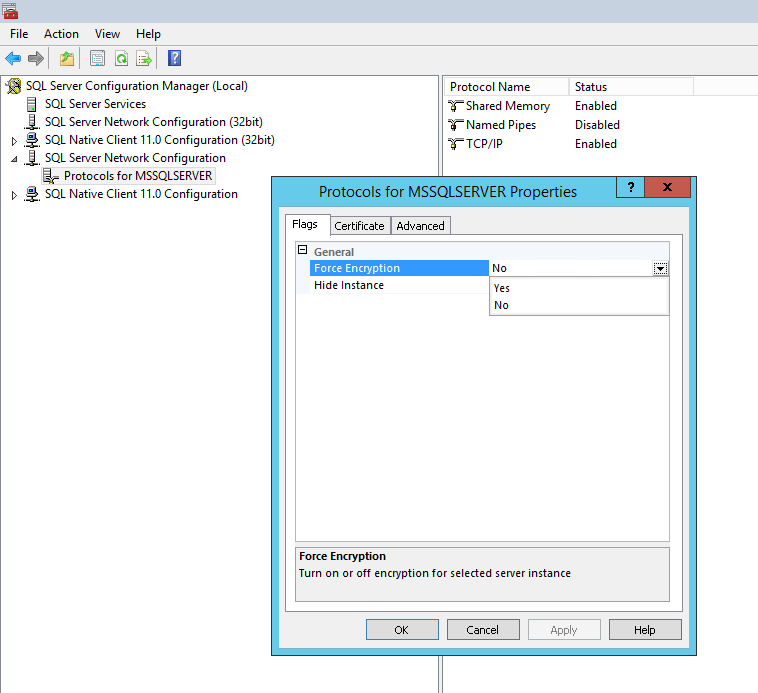
Configure the server(s) to force all incoming connections to use SSL/TLS so that any clients that do not support this will fail to connect. In SQL Server Configuration Manager, set the
ForceEncryptionparameter to "Yes" in the Protocols section.
This solution is not bullet-proof. The database links are generally a potential security risk, when the user permissions are not configured properly and e.g. xp_cmdshell with admin rights is accessible on some of the database nodes. For more information please refer to https://blog.netspi.com/how-to-hack-database-links-in-sql-server/.
For more information how to create a certificate please see the chapter System communication hardening