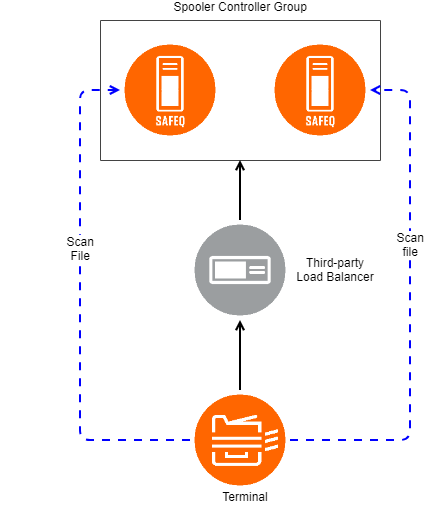
The Requirements for a Third-party Load Balancer
The solution must be based on software or hardware load balancer in the customer's network (black box Failover and Load balancing). The unit of failover and load balancing is one Spooler Controller Group. The Spooler Controller Group is represented from the perspective of MFDs by one and only one virtual IP address or FQDN (reverse lookups have to be configured) which is held by the load balancer. This virtual address will be used by MFDs and Dispatcher Paragon Terminals.
Following requirements are expected to be delivered by the load balancer for Terminal Failover:
- It shall make failover decision based on the state of appropriate Windows Services as reported by Service Control Manager of individual servers running SPOC/TS services AND/OR based on the availability of selected TCP ports. If TCP based monitor is in place, required ports for monitoring are 5555 (for SPOC service) and 5022 (for TS service). The TCP monitor must finish connection after SYN - ACK with RST, not with FIN. Our recommendation for monitoring period is 5 seconds with node considered down after 3 unsuccessful attempts. Node shall not be considered up immediately but after defined time which must be based on real time required for Management/Site Server to start.
- The load balancer shall honor affinity between MFDs and particular SPOC/TS service instances in the Spooler Controller Group based on the prior decisions made by the load balancer and configurable timeout window. I.e., when the load balancer decides to connect an MFD with a particular SPOC/TS service, it must connect the MFD to the same SPOC/TS service if connection (incl. DNS lookup) attempts are made by the MFD before the configurable timeout elapses. Affinity needs to be set for a minimum of 30 minutes.
- The load balancer shall distribute requests among SPOC/TS nodes in the Spooler Controller Group uniformly.
- The load balancer shall distribute requests from MFDs to SPOC/TS based on Network Communication (typically TCP ports 5011 - 5025 and ports for FTP/WebDAV)
- The load balancer shall handle monitoring and reporting of the service failures on its own.
- All inbound communication to SPOC/TS from a single user session (thus from single MFD) must appear under a single source IP address (e.g. load balancer may mask MFD IP address, but the same masked IP must be used throughout the session; it should not happen that one time the IP address of MFD is visible, one time the IP address of load balancer and next time for example the secondary IP address of load balancer).
Health Check
Ports required to be monitored using TCP Half Open health check:
Port | Service | Method |
|---|---|---|
5555 | SPOC Service | TCP Half Open |
5022 | Terminal Server | TCP Half Open |
Ports Pass through
The following ports are required to be passed to a specific node of the load balancer:
Please note, all the ports should be passed to the same node per request window as defined by persistence, please do not split the ports to different nodes.
Both FTP and WebDAV communication goes directly to the current session node and not trough the Load Balancer
Ports | Service | Method | Affinity / Persistence / Stickiness |
|---|---|---|---|
5011 through to 5025 | Terminal Server | Least connection Method | 30 Minutes |
5610 | Terminal Server (WebDAV) | Least Connection Method | 30 Minutes |
21 FTP Implementation is PASSIVE FTP and will require port > 1024 to be passed, refer to FTP explanation below. | Terminal Server (FTP) | Least Connection Method | 30 Minutes |
FTP Tech Note
The most popular FTP implementation is the Passive or PASV mode. PASV-mode FTP connections are the default on most popular browsers. One of the major advantages of PASV mode is that the server does not need to create a new inbound connection to the FTP client. As we’ll see later, this makes PASV-mode FTP a bit more firewall-friendly.
A PASV mode FTP sequence of events would go like this:
- FTP client: This opens random response ports in the high number range. (For the purposes of this example, we’ll assume ports TCP 6000 and TCP 6001.)
- FTP client: This sends a request to open a command channel from its TCP port 6000 to the FTP server’s TCP port 21.
- FTP server: This sends an “OK” from its TCP port 21 to the FTP client’s TCP port 6000. The command channel is now established.
- FTP client: This sends a PASV command requesting that the FTP server open a port number that the FTP client can connect to establish the data channel.
- FTP server: This sends over the command channel the TCP port number that the FTP client can initiate a connection to establish the data channel. In this example, the FTP server opens port 7000.
- FTP client: This opens a new connection from its own response port TCP 6001 to the FTP server’s data channel 7000. Data transfer takes place through this channel.
Note that the PASV-mode FTP client initiates all connections. The FTP server never needs to create a new connection back to the FTP client.
Firewalls and FTP
FTP modes pose distinct security challenges, depending on whether you’re the client-side or the server-side firewall administrator.
PORT-mode FTP client-side firewall
How do you handle PORT-mode requests made from your FTP clients?
You need to allow both inbound and outbound connections to support PORT-mode FTP client requests made from behind your firewall:
- Outbound: TCP port 21
- Inbound: TCP ports 1024 and above
Dispatcher Paragon settings
- Log in to the Dispatcher Paragon management interface with sufficient rights to administer printers (for example, "admin").
- Go to System > System settings
- Set property to enabled and save the configuration.
Terminal Server settings
Please note that it is assumed all the SPOC servers that are part of the NLB group are also in SPOC Group configuration.
Configuration file on Terminal Server nodes
Perform these steps on all Dispatcher Paragon servers that are part of the Spooler Controller group:
- Set Dispatcher Paragon Terminal Server to use the Load Balancer's virtual DNS name:
- Edit the file <SafeQ_dir>\SPOC\terminalserver\TerminalServer.exe.config.
- Set the Load Balancer's virtual DNS name in the networkAddress parameter.
Into the AppSettings section of the config file add new scanServerIp parameter and set it to the physical IP address of the local TS node.
<add key="scanServerIp"value="physical_IP_address"/>- Save the file.
- Restart Dispatcher Paragon Terminal Server services to apply the settings.
Additional Dispatcher Paragon Configuration
Finish Dispatcher Paragon configuration by following Configuring Dispatcher Paragon for Network-level Terminal Failover.