Before using this guide, it is recommended to read Enhanced Password Protection which offers enhanced protection of passwords.
It is a good security practice to regularly change database access credentials. Whenever the database user password is changed, it is necessary to update connection properties on several places. The article below provides guidelines for:
- PostgreSQL server
- MS SQL Server with SQL authentication
- MS SQL Server with domain authentication and service account
Internal accounts
There are several SQL logins in the database, which were created automatically during installation by Dispatcher Paragon installer. Those are SQL logins, not domain accounts. In the text below, those accounts are highlighted in a box like this one.
How to Encrypt Password
Passwords in Configuration Files
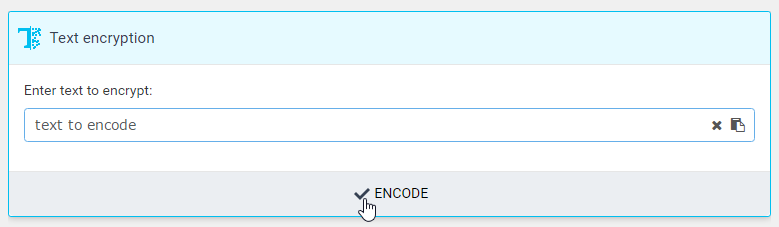
Passwords in the configuration files can be in plain text or encrypted by the utility provided by Dispatcher Paragon as a widget on Dashboard:
- Sign into Management Service interface as an administrator (into a tenant scheme if it is in a multi-tenant environment).
- Stay on Dashboard.
- Find the Text Encryption widget or enable it (click the Add widget button).
- Enter the text to encrypt.
- Click the Encode button at the bottom of the widget.
- Copy the text to the clipboard or transcribe it and replace the original password in the property file.
Passwords in Database
- Passwords in the database are in plaintext.
Dispatcher Paragon Management Service
Refer to page Dispatcher Paragon server requirements for details about all user accounts used by Dispatcher Paragon.
Dispatcher Paragon Management Service - SQL Authentication
Use this procedure to change password for:
PostgreSQL server
MS SQL Server with SQL authentication
For MS SQL Server with domain authentication skip this section. Continue with Dispatcher Paragon Management Service - Domain Authentication instead.
STEP 1 - CONFIGURATION FILES
When using SQL authentication (not domain authentication), update the following configuration files:
- <install_dir>\Management\ims\application.properties:
- spring.datasource.password – password of a user account for IMS database, typically a database with suffix _IMS.
 This is the account provided by the customer.
This is the account provided by the customer.
- spring.datasource.password – password of a user account for IMS database, typically a database with suffix _IMS.
- <install_dir>\Management\conf\safeq.properties:
- database.global.management.password – password for a common connection to the database.
 This is the account provided by the customer.
This is the account provided by the customer. databaseWarehouse.global.management.password – password for a common connection to the database.
 This is the account provided by the customer.
This is the account provided by the customer.Internal accounts
Those accounts were created automatically during installation by Dispatcher Paragon installer. Those are SQL logins, not domain accounts.
- database.cluster.management.password – password of a cluster management user, typically called cluster_mngmt).
- database.cluster.guest.password – password of a cluster guest user, typically called cluster_guest).
databaseWarehouse.cluster.management.password – password of data warehouse guest user, typically called cluster_guest).
databaseWarehouse.cluster.guest.password – password of data warehouse guest user, typically called cluster_guest).
- database.global.management.password – password for a common connection to the database.
- <install_dir>\Management\validator\conf\DBValidator.properties:
- connectionInfoSQ.userPassword – password for a common connection to the database.
 This is the account provided by the customer.
This is the account provided by the customer. - connectionInfoDW.userPassword – password for a common connection to the database.
 This is the account provided by the customer.
This is the account provided by the customer.
- connectionInfoSQ.userPassword – password for a common connection to the database.
STEP 2 - DATABASE
The procedure slightly differs on MU 8 or older, refer to Recovery of databases documentation, Reconfiguring the SQDB6 Database section.
Execute the following query to reset stored procedures' connection strings:
For PostgreSQL:
PostgreSQLSELECTcluster_mngmt.spu_recover_tenant_db_passwords();For MS SQL Server:
MS SQL ServerEXECcluster_mngmt.spu_recover_tenant_db_passwords;
Execute database validator:
- Execute the following query
For PostgreSQL:
PostgreSQLSELECTcluster_mngmt.spu_clean_validator_tables();For MS SQL Server:
MS SQL ServerEXECcluster_mngmt.spu_clean_validator_tables();
- Navigate to <install_dir>\Management\validator\conf\DBValidator.properties and verify the database passwords.
- Navigate to <install_dir>\Management\validator\bin\validatorRunner.exe
- Run it.
More information: DB Validator Tool
Dispatcher Paragon Management Service - Domain Authentication
Use this procedure to change password for:
- MS SQL Server with domain authentication. The installation followed this procedure: (6.0.105) Installing Dispatcher Paragon Management Server on external MSSQL using domain users
STEP 1 - CONFIGURATION FILES
When using DOMAIN authentication (not sql login authentication), update the following configuration file:
- <install_dir>\Management\validator\conf\DBValidator.properties:
- connectionInfoSQ.userPassword – password for a common connection to the database.
 This is the account provided by the customer.
This is the account provided by the customer. - connectionInfoDW.userPassword – password for a common connection to the database.
 This is the account provided by the customer.
This is the account provided by the customer.
- connectionInfoSQ.userPassword – password for a common connection to the database.
- <install_dir>\Management\conf\safeq.properties:
- database.global.management.password – password for a common connection to the database.
- databaseWarehouse.global.management.password – password for a common connection to the database (set manually only if not already using the variable in the configuration file)
- <install_dir>\Management\ims\application.properties:
- spring.datasource.password – password for a common connection to the database (update only if the configuration option is present in the file, no change required otherwise).
STEP 2 - DATABASE
Internal accounts
Internal accounts are users without passwords when using domain authentication. There is no need to update any passwords.
Reference: https://docs.microsoft.com/en-us/sql/relational-databases/databases/contained-databases
Execute database validator:
Perform the steps below only if data warehouse is deployed on a different SQL Server, SKIP THEM OTHERWISE.
- Execute the following query
For PostgreSQL:
PostgreSQLSELECTcluster_mngmt.spu_clean_validator_tables();For MS SQL Server:
MS SQL ServerEXECcluster_mngmt.spu_clean_validator_tables();
- Navigate to <install_dir>\Management\validator\conf\DBValidator.properties and verify the database passwords.
- Navigate to <install_dir>\Management\validator\bin\validatorRunner.exe
- Run it.
More information: DB Validator Tool
STEP 3 - WINDOWS SERVICES
Update service account password on affected Windows services - run services.msc, see "Log on" tab, restart the service after the change is applied:
- Dispatcher Paragon Infrastructure Service
- Dispatcher Paragon LDAP Replicator
- Dispatcher Paragon Management Service
Dispatcher Paragon Management Service - etcd (not needed from Build 67 and above)
- Open PowerShell window and navigate to directory: <install_dir>\Management\etcd
Run this command to dump etcd content
rmetcddump.ps1-easilentlycontinue; .\etcdctl.exels/ | %{" .\etcdctl.exe --endpoint http://127.0.0.1:2379 update $($_ -replace `"/`", `"`") `"$(.\etcdctl.exe get $_)`""|out-fileetcddump.ps1-append}- Open newly created file etcddump.ps1 for editing
- Adjust password value on those lines:
This is the account provided by the customer:
.\etcdctl.exe --endpoint http://127.0.0.1:2379 update encryptedUserPassword "code,104,119,-55,-123,-120,-2,-11,-38,44,-42,70,123,-64,-125,30,69"If you have SafeQ DataWarehouse database deployed on a different server (MSMD deployment), adjust also this line:
.\etcdctl.exe --endpoint http://127.0.0.1:2379 update DWencryptedUserPassword "code,104,119,-55,-123,-120,-2,-11,-38,44,-42,70,123,-64,-125,30,69"Internal accounts:
Internal acounts
Those accounts were created automatically during installation by Dispatcher Paragon installer. Those are SQL logins, not domain accounts.
.\etcdctl.exe --endpoint http://127.0.0.1:2379 update encryptedClusterPassword "code,-57,-15,18,97,115,-62,79,17,-93,-27,25,13,61,124,37,34".\etcdctl.exe --endpoint http://127.0.0.1:2379 update encryptedClusterGuestPassword "code,-68,22,-35,-10,33,-82,24,42,-64,81,-56,112,54,83,121,76".\etcdctl.exe --endpoint http://127.0.0.1:2379 update encryptedTenantPassword "code,-105,-107,-24,-63,-8,29,43,-21,14,64,68,91,-106,60,-59,94"If you have SafeQ DataWarehouse database deployed on a different server (MSMD deployment), the following lines are also present:
.\etcdctl.exe --endpoint http://127.0.0.1:2379 update DWencryptedClusterPassword "code,-57,-15,18,97,115,-62,79,17,-93,-27,25,13,61,124,37,34".\etcdctl.exe --endpoint http://127.0.0.1:2379 update DWencryptedClusterGuestPassword "code,-68,22,-35,-10,33,-82,24,42,-64,81,-56,112,54,83,121,76"
Run this command to restore etcd content:
powershell.exe-executionpolicybypass .\etcddump.ps1Review the content using this PowerShell command:
.\etcdctl.exels/ | %{write-host"$($_): $(.\etcdctl.exe get $_)"}
Dispatcher Paragon Management Service - Apply the Change
The following services need to be restarted to apply the changes:
- Dispatcher Paragon Management Service
- Dispatcher Paragon Infrastructure Service
Dispatcher Paragon Payment System
Dispatcher Paragon Payment System - SQL Authentication
Use this procedure to change password for:
PostgreSQL server
MS SQL Server with SQL authentication
For MS SQL Server with domain authentication skip this section.
The passwords must be changed in configuration files when the user password of a connection to the database is changed:
- <install_dir>\YPS\ps-conf\environment-configuration.properties
database.password – the password of a user for a common connection to the database (typically, a default user with the username "postgres" or "sa")
Dispatcher Paragon Payment System - Domain Authentication
No extra step required.
Dispatcher Paragon Payment System - Apply the Change
The following services need to be restarted to apply the changes:
- Dispatcher Paragon Payment System Service